USB Powered devices : A survey of sidechannel threats and countermeasures
※ 해당 논문을 분석하여 작성한 글입니다.
논문 선정 이유
전자 기기와 IOT의 빠른 확산은 일상적인 삶에 새로운 혼란들을 야기한다. 이와 같은 대부분의 기기들은 USB에 의존하며 두 가지의 주요 기능(데이터 전송, 전력 충전)을 가진다.
일반적으로 대부분의 사용자들은 자신의 모바일 디바이스를 신뢰하지 못할 USB 포트에 연결하는 것에 대해 심각하게 받아들이지 않으며 이는 악의적인 공격자들이 이용하여 민감한 정보를 훔칠 수 있다.
-> side-channel attack에 대해 알아보고자 이 논문을 선정하게 되었다.
Introduction
Overview and categorize the main works exploiting side-channel vulnerabilities in USB connections.
Analyze the current countermeasure presented in the literature to prevent this class of attacks.
Furthermore, while traditional attacks need to actively take control of the targeted device,
side-channel attacks are passive and hard to detect.
For instance, an attacker may compromise a power bank or a public charging station by adding an integrated module to delivering malicious payloads (i.e., active attack) or to collect power consumption traces (i.e., passive attack).
Background
1) USB ecosystem
Universal Serial Bus is the most popular standard used to wired connect peripheral devices (i.e., USB devices) to a central host and transmit information.
- versions 1.1, 2.0, 3.0, 3.1, 3.2 up to the latest version 4.0
a. Human layer
This layer involves all the actions and the interactions between the host and the enddevice.
Attackers can exploit this layer through social engineering attacks or by human errors.
b. Application layer
It is composed of the user-level programs and software on the host and the device sides.
Main attack: code Injection/Exfiltration
c. Transport layer
It regulates the data transmission policies between the two entities involved in the communication.
Main attack: Protocol Masquerading/Corruption
d. Physical layer
It comprises signals representing communications occurring over the USB bus at the lower level.
Main attack: Signal Eavesdropping (USB snooping), Signal Injection
Host : power supplier (power bank, wall socket, a smartphone, or a general device with charging capabilities)
End-device : the device powered by the host (a peripheral device or the smartphone in a recharging scenario.)

2) Side-channel attacks
USB standard is designed without considering security. ... USB is used in a wide range of applications, ranging from critical applications (e.g., Industrial Control Systems) to home applications (e.g., IoT devices)
It is important to identify security threats arising from the insecure USB standard design and develop new security solutions to prevent potential malicious events.
Side channel attacks were originally implemented to break cryptographic primitives exploiting common patterns on the power consumption to reverse the algorithm (e.g., Simple Power Analysis and Differential Power Analysis).
However, in recent years side- channel attacks have also been implemented to profile actions in different encrypted network traffic scenarios such as smartphone user actions, IoT actions, and internet traffic
Side-channel attacks
Attacks that exploit the physical characteristics of an uncontrolled system to compromise the confidentiality or integrity of the system.
A side-channel attack’s main idea is to leverage uncontrolled physical characteristics produced by the system during its functioning (power consumption, noise, timing) to identify confidential information and functioning patterns.
a. Passive / active
passively listen and leak information / modify the system’s normal function or tamper with it
b. Physical properties / logical properties
Physical properties (e.g., power consumption or electromagnetic emanation) /
logical properties (e.g., statistics provided by the operating systems)
c. Local / Remote (the position of the attacker according to its target)
direct control of the device / only rely on software execution on the targeted device

Threat model
As modern mobile devices’ applications provide more and more advanced functionalities and personalized user experience, they are also increasingly becoming energy demanding. The intensive usage of those apps combined with their need for energy often causes batteries to be quickly depleted.
-> The increasing demand for ways for users to charge their devices led to the growth of the mobile charging industry and the installation of mobile charging stations in public places where every- body can access them,
Threat model -> where a mobile device is connected to a USB port via a cable.
Attacker -> is able to observe one or multiple side-channels by controlling or by accessing the surrounding of the USB charging port.
Host device -> device that provides a USB port (public, charging station, power adapter, USB hub, desktop PC)
End device -> portable device (laptop, smartphone, tablet computer, portable hard drive, keyboard) powered by such USB port
Channel -> The USB connection cable

Case 1: Attacker that has control over a host’s USB port, the USB cable, or the USB hub, can identify three attack scenarios.
a. Public charging station
USB ports on appliances available in public places -> airports, chopping malls, entertainment venues
The attacker tampers with charging stations and it exploits users' default trust in the person providing the charging station.
b. Semi-public station (e.g., hotel)
Devices that USB ports cannot be fully attended by users all the time.
(e.g., in a hotel, a user has no control nor can inspect the assigned room before check-in... During this time, an attacker can access the room and deploy its attack tools on the available USB ports. )
c. Chargers borrowed from others
Attacker could have previously tampered with such a charger and deployed its attack tool.
Case 2: Attacker does not have direct control of the USB port
(가정) Attacker can access the immediate surrounding of such a USB port, the end device, or the channel.
Attacker can place a probe (e.g., antenna, sensor) and observe wireless side-channels such as electromagnetic, radio-frequencies, or sound emis- sion from either the end device, the channel, or the host.
Attacks
Categorizing the work according to the type of side-channels that an attack relies on.
The side-channel-based attacks considered in this survey are summarized in Table 1 .

1. Electromagnetic emissions (EM)
Electromagnetic (EM) emissions (or radiations) are waves that can propagate in space, and they include visible light, radio waves, microwaves, etc.
Generated by - electrons’ flow (e.g., from the data transfer on a USB cable that acts as an antenna.)
Attackers can exploit this phenomenon to extract cryptographic keys and keystrokes recognition.
EM signals often propagate through conduction and radiation; these signals can be intercepted using sensors, such as a near-field probe or an antenna. Using these sensors allows the EM signal to be transferred into a current signal, which is post-processed to remove noise, and limit the frequency band in order to apply the EM analysis.
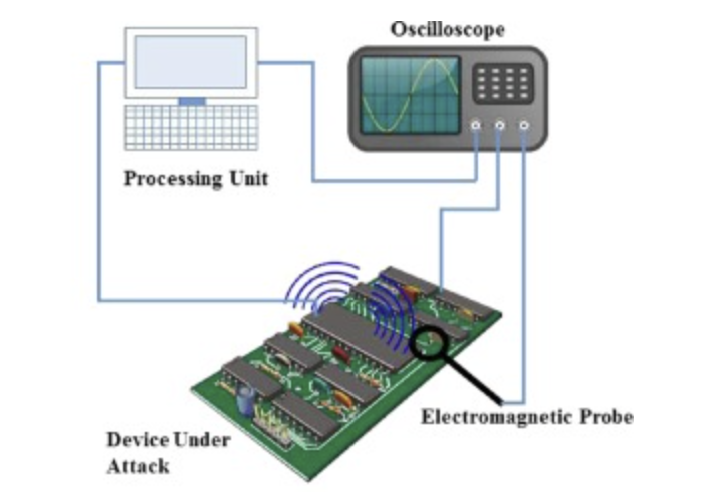
The quality of the received signal is usually improved if the used sensor is shielded from unwanted frequency bands, or other EM interferences. Post-processing of the signal may include filtering frequency bands that are not related to the targeted critical data path, which requires prior knowledge of the frequency band that holds the information. In order to obtain that knowledge, a spectrum analyzer is commonly used to identify carriers and noise; then a post-processing filter can be tuned only to allow critical information to pass. Figure 8.9 shows an illustration of a measurement setup for the EM attack.
1.1. Attacking elliptic curve-based encryptions
The Elliptic Curve Digital Signature Algorithm (ECDSA) security relevance is meaningful since important companies employ elliptic curve encryption in their payment systems.
ECDSA implementations on mobile devices are vulnerable to electromagnetic and power side-channel attacks.
The authors consider two similar threat models a and b.
a. End device lying over a coil
(!!) The coil senses the electromagnetic emissions from the end device’s processor while performing.
These traces can be acquired by the attacker’s PC via an inexpensive device (i.e., a sound card)
Attackers can extract the ECDSA signature key used by the OpenSSL library running on iOS and Android devices.
b. End device connected to a USB cable
(!!)The authors perform the same attack by relying on power analysis over the USB cable.
Belgarric et al. [47] show that, for elliptic curves over the prime domain, private keys on smartphones can be recovered using electromagnetic side-channels and lattice simplification techniques.
- USB cable is assumed to be the only I/O interface of the end device (i.e., smartphone) and it is used as a trigger for the oscilloscope via self-written software installed on the targeted device
- Such software sends a trigger signal through the end device’s USB interface (connected to the oscilloscope’s trigger port) and immediately invokes the Bouncy Castle signature function.
* Bouncy Castle is a collection of APIs used in cryptography. It includes APIs for both the Java and the C# programming languages.
- The electromagnetic radiations are then acquired and analyzed by manually observing additive operations in the collected traces.
1.2. Keystrokes recognition
Considering a USB wired keyboard as the end device, researchers show how to infer keystrokes from electromagnetic emanation side-channel.
-> Extensive study on this kind of attack by testing its feasibility on different keyboard technologies, among which PS/2, USB, laptop, and wireless.
( The technique generally used to detect compromising emanations is based on a wide-band receiver, tuned on a specific frequency. However, this method may not be optimal since a significant amount of information is lost during the signal acquisition. Approach is to acquire the raw signal directly from the antenna and to process the entire captured electromagnetic spectrum)
2. Electric power analysis
Consists of measuring the electric energy provided by a USB port to the end device.
Since a USB port delivers energy to an end device using direct current, an attacker can rely on the measurement of electrical quantities: current (in Ampere), electric re-sistance (in Ohm), the difference of potential (in Volt), and power (in Watt).
Explore the electric power analysis-based attacks that have been exploited to retrieve cryptographic keys, exfiltrate data, and infer content from either host or end devices.
The attacks targeting host devices typically relying on voltage variance measurement since they assume an open circuit scenario (i.e., no electric current flows from the 5V to GND pins).
2.1. Data exfiltration
To exfiltrate private information from an Android device, use the power consumption during the charging process as a covert channel. In particular, this attack is carried out while the end device is in an idle situation (i.e., no user interaction, screen off) to achieve stealthiness. When the battery level is high enough, observed that part of the unused electric power supplied by a USB port is directly used to power other mobile devices’ functionalities. The attack consists of encoding a message (i.e., the targeted private information) as temporized energy over-consumption on the end device, which can be observable (then decoded) from the host device.
a. PowerSnitch
A malicious application, named PowerSnitch, installed on the end device, converts the information to exfiltrate in binary code. According to the value of the bit to transmit, the PowerSnitch app generates a CPU burst, which causes the over consumption for a predetermined time interval. Moreover, the PowerSnitch app does not require any special permission except accessing the information to exfiltrate.
b. Power supplier control
On the host device, the attacker controls the power supplier (i.e., USB port) and can measure the electric current provided to the end device. The attacker can process the signal from the energy traces, decode the binary transmission, and reconstruct the original information.
2.2. Web pages identification
Attacker could steal user information while a user is using a mobile charging station to charge a smartphone.
The attack works even without using the data transfer function of the USB cable.
The attack leverages a malicious charging station and can identify the web pages loaded by the user while charging with the malicious station.
Browsing web pages using Tor is considered secure, but it is not immune to power sidechannel attacks on USB cables.
In an extended version of the attack, can identify the websites the user visited through Tor, even hidden services, with a higher accuracy rate than ordinary websites.
2.3. Juice Filming Charging attacks (JFC)
The threat model presented in this survey. These attacks rely on Mobile High-definition Link (MHL) technology, which activates automatically when an Android device or iPhone is connected to a projector via the USB cable. The JFC attack exploits the MHL standard to turn the USB cable into a video cable (VGA or HDMI)
Result : the end device’s screen and user inputs can be obtained by the host device (e.g., modified malicious charger) via the USB data connection. When an end device is connected to a malicious charger that enables MHL, the letter one can record the user’s input (i.e., taps on a touch-screen) and screen activity. To make this attack even more dangerous, JFC cannot be detected by antimalware software, and it works on both iOS and Android end devices.
Countermeasures
Different countermeasures to cope with keystrokes inference attack, which can also be valid against other attacks relying on EM emissions side-channels.
1. Countering EM emissions
First solution.
Properly shielding keyboards to reduce electromagnetic radiation without affecting their normal function significantly. However, this solution dramatically increases production costs since all in- ternal components of a keyboard and cable have to be shielded and the host device.
Second solution.
To secure the surrounding area around a vulnerable keyboard. This can be achieved by shielding the room (which may still be costly) or establishing a physically secure perimeter (e.g., one hundred meters).
Both these solutions would stop attackers from observing EM emissions. Thus both these solutions can also counter other EM emanations-based attacks.
Third solution.
To input high-frequency filtered matrix sig- nals into the keyboard, which limits the electromagnetic radiation to a certain extent. However, with this solution in place, electromagnetic emanations are noisy but still present, and they can further be analyzed with the aid of machine learning.
Fourth solution
The use of two-ways encryption for communication is a possible software-based countermeasure to protect user data from EM emissions side-channel at- tacks. Even if EM emissions are still measurable, the attacker will not retrieve the encrypted communication content.
Keyboards’ communication chips should be modified to implement encryption. However, encryption alone may not be enough: 1) weak encryption schemes can be broken; 2) an attacker can still leverage other side-channels information (e.g., keystrokes timing) to profile the user behavior. It is worth noticing that users can use only the second coun- termeasure, despite not being always possible, can be implemented by users while the other ones have to be implemented by the manufactures (i.e., they need special hardware modules).
EM emission side channel is not only used to carry out attacks but also to detect malicious end devices disguised as USB flash drives (e.g., Rubber Ducky, Keylogger).
2. Electric side-channels
To cope with Charger-Surfing and other similar side-channel attacks, Cronin et al. propose both software and hardware-based solutions that take into account the specific characteristics of such attacks.
a. randomizing the key positions on touchscreens.
The power side-channel produced by button animations can be addressed with the first proposed software-based countermeasure. This kind of countermeasure has already been widely adopted in many financial savings applications. However, applying this method to lock screen password/PIN negatively affects the usability of end devices.
(Users would have to assess the new keys positions every time they are randomized, which is inconvenient in time-critical and repetitive operations, such as screen unlocking and small payment authorizations. ... not recommend!)
b. To remove the button input animations.
This solution would not provide feedback to the user on whether the button was correctly pressed.
c. adding noise on the screen
This countermeasure consists of adding noise on the screen, for example, by using an animated background.
It has two downsides:
1) animated backgrounds can only be used on the lock or home screens, so they cannot secure the use of on-screen keyboards (e.g., messaging); 2) if the animation is predictable (e.g., in a loop), the generated noise can be filtered out with enough samples.
As a hardware- based countermeasure, mitigate the power leakage by inserting a low-pass filter into the charging circuit. This solution filters out the frequencies used to carry out Charger-Surfing attacks.
d. a Malboard : a malicious hardware USB device
Such a device can automatically inject keystrokes (e.g., malicious commands) with a tagret. User’s behavioral characteristics into a host device. By mimicking the user’s behavior, Malboard can elude detection mechanisms that continuously verify the user’s identity via her keystrokes

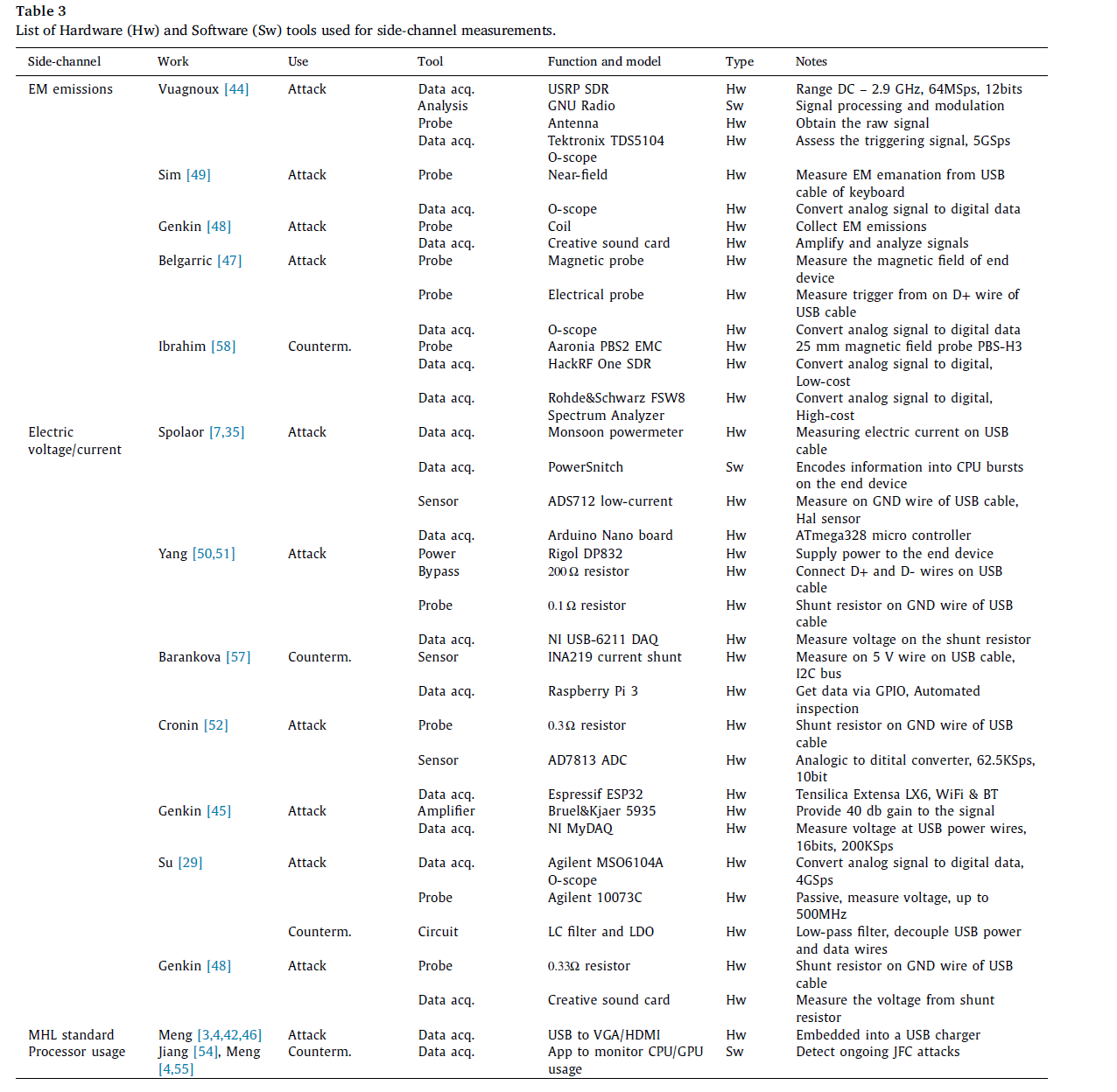
Tools for side-channel measurements
To foster new researchers approaching side-channel analysis, this paper listed and discussed the various approaches in the state-of-the-art.
EM emissions relies on several solutions for sensing/probing and data acquisition.
1. Electromagnetic emissions
Attacks that aim to infer cryptographic keys also rely on similar experimental settings: a probe to sense EM emission and a data acquisition device. In particular, Belgarric et al. also use an oscilloscope for data acquisition from a magnetic probe placed near the end device’s processor.
2. Electric voltage/current
Considering the side-channels related to electric properties, thih paper distinguish between two typical approaches:
• Current measurement on a circuit closed by a shunt resistor (i.e., voltage drop) or Hall-effect sensor (i.e., on the 5v or GND wires of a USB cable).
• Voltage variance measurement from an open circuit (e.g., from 5v and GND of a USB port);
Discussion and future directions
While the former side-channel needs probes to be physically attached or modify a USB port, cable, or charger (i.e., shunt resistor for electric current and probe on two USB wires), the latter can be measured wirelessly with magnetic or near field probes at a short middle distance from the target device. In both cases, such attacks are passive. Therefore they are challenging to be detected via software countermeasures.
To mitigate electric power side-channels, users can use frequency filters (e.g., LC filter and LDO) on the USB power wires or decoupled power sources (e.g., on USB hubs). Avoiding EM emissions can be particularly challenging, and it requires joined efforts from manufactures and users.
EM- signal과 side-channel attack에 대한 공부를 더 해야할 것 같다. 하드웨어 관련 개념들 또한 많이 알아야 할 것 같다.
논문에서 사용되는 약어들에 더 익숙해지면 좋을 것 같다.. (et.al means and others, i.e. means in other words)
Reference
https://www.sciencedirect.com/topics/computer-science/electromagnetic-signal
'SWLUG > paper analysis' 카테고리의 다른 글
| [논문분석] 김기훈, and 박재표. "ICT 기반 전력시스템에서 APT 공격탐지를 위한 온톨로지 모델링." 한국산학기술학회 논문지 25.2 (2024): 764-770. (10) | 2024.10.29 |
|---|---|
| [논문분석] 이지은. "모빌리티 강건 주행을 위한 인공지능 기반 노면 상태 판단 알고리즘 개발." 국내석사학위논문 순천향대학교, 2023. 충청남도 (16) | 2024.09.24 |
| [논문 분석] Inferring Browsing Activity on Smartphones (0) | 2024.05.21 |
| [논문 분석] Charger -Surfing (2) | 2024.04.30 |
| [논문 분석] IoT Sensor가 연결된 국방정보통신망의 사이버 보안 연구 (1) | 2024.04.27 |